Sentinel Keys
|
New to Sentinel EMS?
|
What is a Sentinel Key?
A Sentinel key is a hardware- or software-based license container that may include:
>One or more licenses that provide access to protected applications
>Protected memory that can only be accessed from protected applications
>An encryption engine that can only be used by protected applications
The Sentinel key must be accessible to the machine on which a protected application runs, either by a local connection or a network connection.
Keys are added to the Sentinel Keys page when the vendor activates an entitlement or checks in a C2V file.
Prerequisites for Checking In a Sentinel Key
>A role that includes Activation Management permissions. At minimum, you need the Add permission. For details, see Roles.
>Access to one of the following:
•The Customer-to-Vendor (C2V) file generated on the end user's machine.
•The Sentinel HL Key containing the license.
Sentinel Key Status
The Status attribute for a Sentinel key can be one of the following:
| Status | Description |
|---|---|
| Enabled | When you check in a C2V file, the status of the Sentinel key is set to Enabled. |
| Disabled | Relevant only for Sentinel HL (Driverless configuration) keys. Indicates that tampering was detected. Sentinel LDK Envelope run-time module disabled the key because it determined that the user attempted to tamper with the key or with the protected application. For more details, see Sentinel LDK Software Protection and Licensing Guide. |
| Blocked | Relevant only for Sentinel keys that were migrated from Sentinel LDK-EMS in a disabled state. This may occur the key was disabled using a Sentinel LDK-EMS web service prior to migration. Blocked keys are read-only and cannot receive updates. However, customers can continue using these keys with the existing data. |
| Cloned | Relevant only for Sentinel SL keys. Indicates that Sentinel LDK Run-time detected cloning and disabled the affected licenses. This prevents an end user from logging on to the software for which cloned licenses are detected. The end user must contact your vendor representative and submit a C2V file from the machine on which the cloned license was detected, together with their Product Key, to have the cloned key updated and the product activated. For more details about clone protection, see Sentinel LDK Software Protection and Licensing Guide. |
| Out-of-Sync |
Relevant only for CL keys when using Produce and Push. Indicates that the push operation failed for the service-hosted cloud licensing key. |
| Virtual Clock Error |
Relevant only for Sentinel HL (Driverless configuration) keys that: > Do not contain a real-time clock (such as Max keys), and >Use time-based licenses (such as Expiration Date, Time from First Use, or Time from License Generation). Indicates that the difference between the system time on the end user's machine and Sentinel EMS is more than 24 hours. This may signify tampering with the time-based licenses. |
Checking In a Sentinel Key
You can check in a Sentinel key using one of the following options:
>A C2V file generated on the end user’s machine. Use this option for Sentinel SL keys or when you do not have physical access to the Sentinel HL key.
>The Sentinel HL key that contains the license. Use this option when you have physical access to the Sentinel HL key. This eliminates the need to receive a C2V file from your customer each time you perform a check-in.
The check-in process securely uploads the key information to Sentinel EMS and confirms any licenses previously activated on the end user’s Sentinel HL or SL key. This information is then used to manage license updates and synchronize orders.
To check in a Sentinel key, your user account must be associated with the same market group as the key you are checking in.
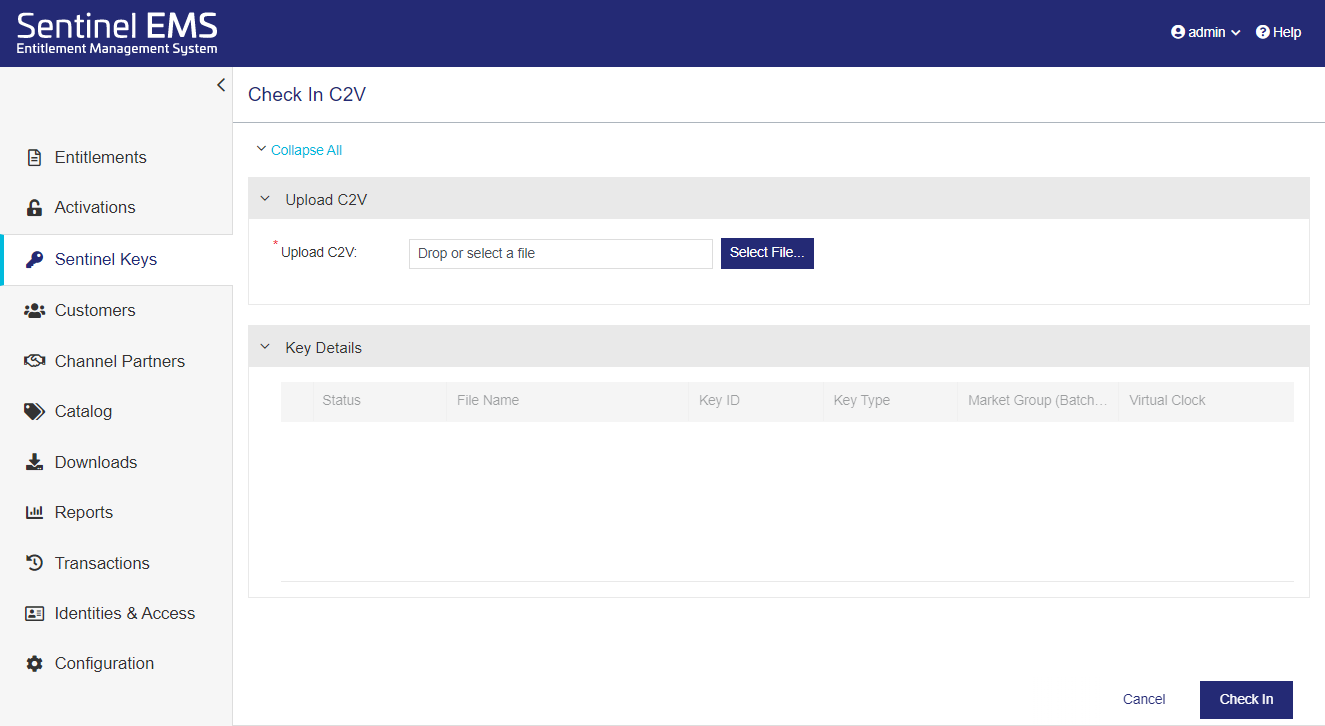
To check in a Sentinel key:
1.From the navigation pane, select Sentinel Keys to view the Sentinel Keys page.
2.Click Check In Keys. The Check In Keys page opens.
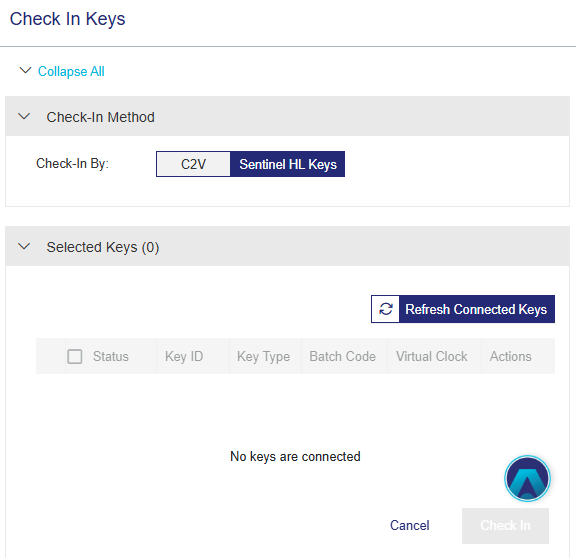
3.Under Check In Method, in Check In By, select one of the following options:
•C2V – to upload a C2V file.
•Sentinel HL Keys – to check in directly from a connected hardware key.
4.Depending on the selected method:
•If you selected C2V: In the Upload C2V box, either browse to select a C2V file or drag and drop a C2V file into the Upload C2V area.
You can safely drop the C2V file when you see a large box that instructs you to drop your file in the box. Sentinel EMS validates the C2V file. If the C2V file is valid, the word C2V is embedded in the Upload C2V box and the Key Details area displays data from the C2V. Otherwise, an error message is displayed.
•If you selected Sentinel HL Keys: From the list of keys, select the check box next to each key to check in.
–To refresh the list, click Refresh Connected Keys.
–If a key cannot be selected, point to the icon next to the Key ID to view the reason.
–To identify a physical key, in the Actions column, click Blink Connected Key.
5.Click Check In.
Viewing C2V Data
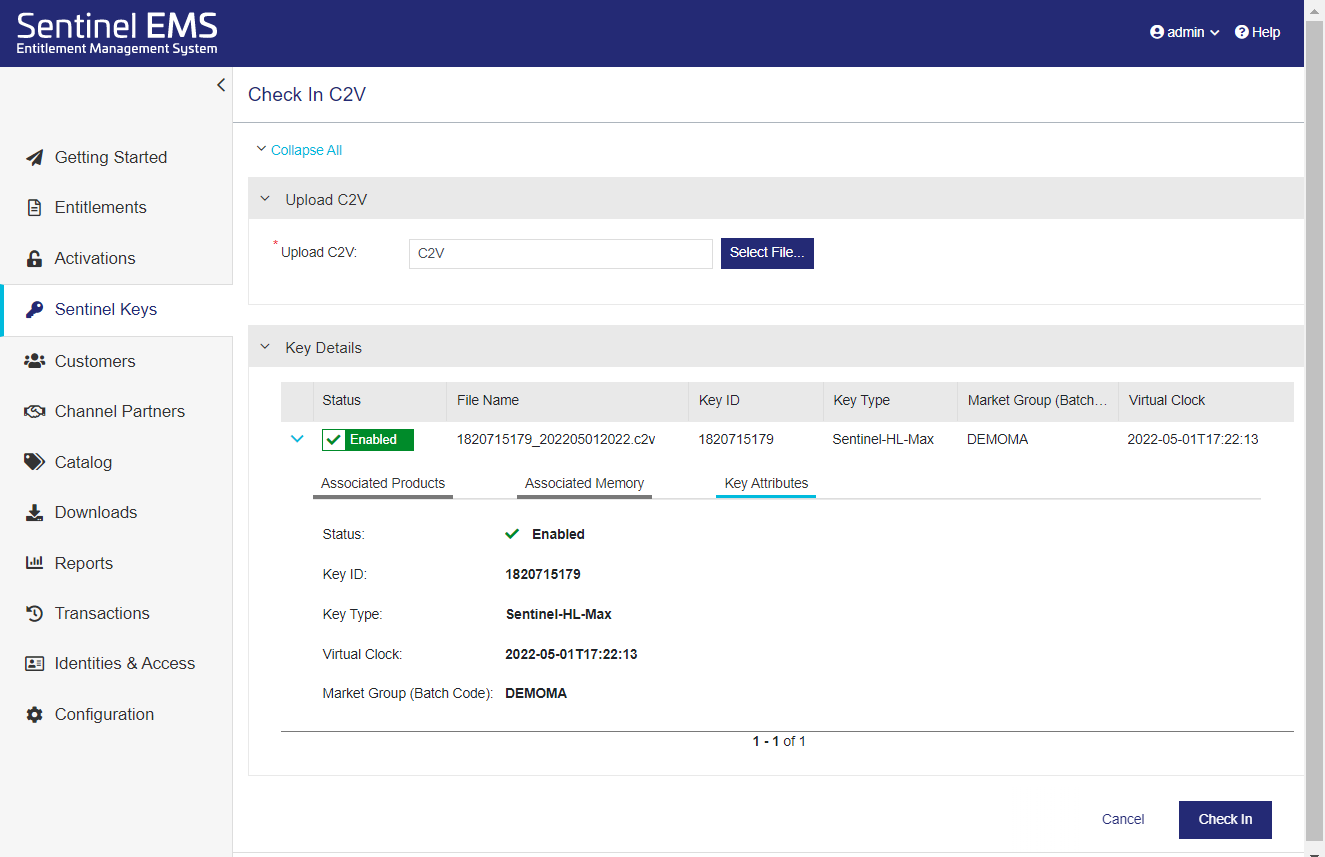
C2V files are encrypted by default. You can use the Check In C2V page to view the data stored in a C2V file.
To view C2V data:
1.From the navigation pane, select Sentinel Keys to view the Sentinel Keys page.
2.Click Check In Keys. The Check In Keys page opens.
3.Under Check In Method, in Check In by, select C2V.
4.In the Upload C2V box, either browse to select a C2V file or drag and drop a C2V file into the Upload C2V area. You can safely drop the C2V file when you see a large box that instructs you to drop your file in the box. Sentinel EMS validates the C2V file. If the C2V file is valid, the word C2V is embedded in the Upload C2V box and the Key Details area displays data from the C2V. Otherwise, an error message is displayed.
5.Expand the Key Details area to view the attributes embedded in the C2V file.
–Expand a product to view its Associated Features.
The following example shows the data available when viewing the content of a C2V file.
Sentinel Key Attributes
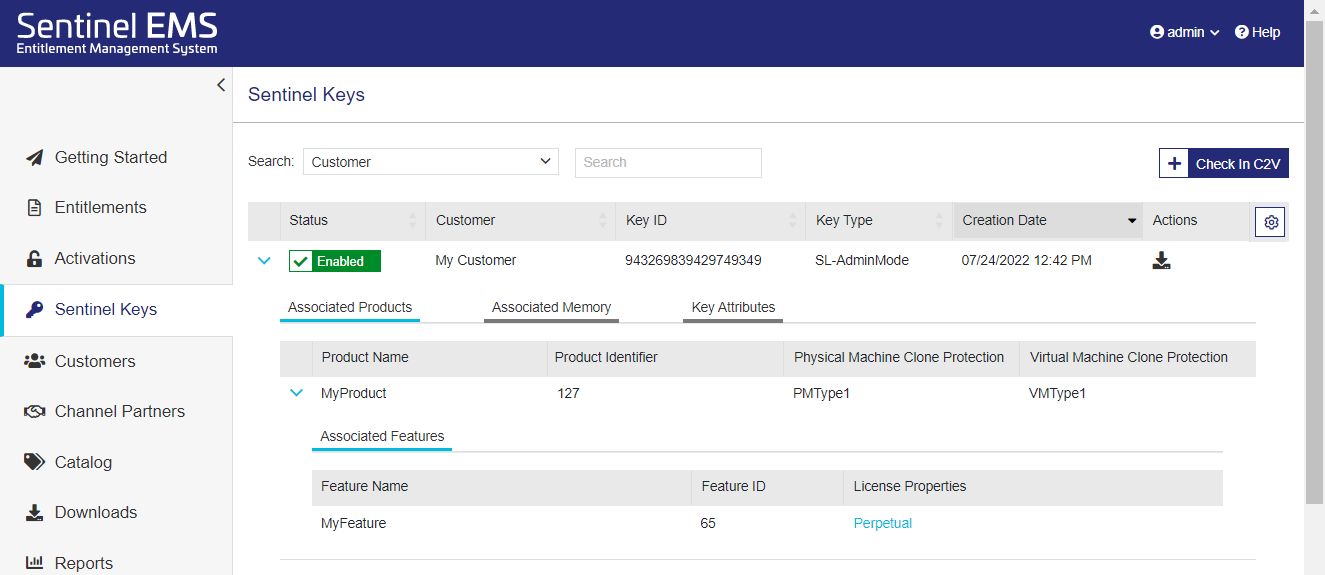
The sections below describe the data that is embedded in a Sentinel key. This data is visible on the Sentinel Keys page. The following image shows an example of Sentinel key data with the Associated Products section expanded.
Associated Products
The following table explains the associated product attributes.
| Attribute | Description |
|---|---|
| Product Name | The name of product included in the entitlement. |
| Product Identifier | The numeric identifier for the product included in the entitlement. |
| Physical Machine Clone Protection |
The clone protection scheme to be used on a physical machine. Default value: Platform Default NOTE If the product was migrated from Sentinel LDK, displays the clone protection scheme defined in Sentinel LDK-EMS prior to the migration. |
| Virtual Machine Clone Protection |
The clone protection scheme to be used on a virtual machine. Default value: Platform Default NOTE If the product was migrated from Sentinel LDK, displays the clone protection scheme defined in Sentinel LDK-EMS prior to the migration. |
Associated Features
The following table explains the associated feature attributes.
| Attribute | Description |
|---|---|
| Feature Name | The name of feature associated with the product. |
| Feature ID | The unique numeric identifier for the feature associated with the product. |
| Custom Info |
The additional information included in the license, evaluated from the license attribute value defined in the entitlement. |
| License Properties |
Enables you to view the properties for the associated license model. NOTE FOR CONCURRENCY If the Network Term attribute was set to No in the associated license model, and the product was activated with support for a Sentinel HL key, then concurrency is implemented with Per Station and Unlimited in the Sentinel key. This implementation ensures that if multiple applications are using the same, locally installed license on a single machine, all of those applications can access the license. Otherwise, if the Network Term attribute was set to Yes in the associated license model, then the defined concurrency limits are implemented. |
Associated Memory
The following table explains the associated memory file attributes:
| Attribute | Description |
|---|---|
| File ID | The numeric identifier that your application uses to refer to the selected memory file. |
| File Type | The read-write permissions for the memory file. For details, see Memory. |
Key Attributes
The following table explains the Sentinel key attributes: The displayed key attributes depend on the type of key.
| Attribute | Description |
|---|---|
| Status | The status of the Sentinel key. For details, see Sentinel Key Status. |
| Customer Name | Name of the customer defined in the entitlement. |
| Customer Identifier | The customer identifier defined in Sentinel EMS. |
| Key ID | The unique, automatically generated, Sentinel key identifier. |
| Key Type |
The locking type, for example, SL-AdminMode or Sentinel-HL-Max. For CL keys, Key Type is set to SL-AdminMode and Hosted Service is set to Yes. |
|
Batch Code |
(Visible only when Viewing C2V Data) The batch code that was defined when creating the product included in the Sentinel key. |
| Virtual Clock |
(Displayed only when available) The date and time when the protected application logged in to the feature. The default time zone is UTC. See also: Reset Virtual Clock |
|
Hosted Service |
Indicates if the Sentinel key is connected to the service-hosted, cloud license manager server, which is hosted by Thales. This requires a subscription to the Sentinel LDK CL Service. When set to Yes, the key is known as a CL key. Possible values: Yes or No |
|
Market Group |
The market group associated with the customer who uses this key. The market group value may be custom-defined, may match your organization's unique batch code, or may match the batch code for Sentinel protection keys with a demo vendor code—DEMOMA. |
| Creation Date |
The date and time that the C2V file was checked in for this Sentinel key or when the product is activated for the first time. The default time zone is UTC. |
| Last Modified Date |
The date and time that an updated C2V file was checked in for this Sentinel key, for example, if the license was updated or when the product is activated for the first time. The default time zone is UTC. |
Actions for Sentinel Keys
The following table lists the actions available for Sentinel keys. Each action is available only for certain conditions, as described below.
| Action | Description | |
|---|---|---|
|
|
Download V2CP |
Downloads the V2CP file that was generated from the C2V file. Available for: Sentinel keys whose status is Enabled, excluding CL keys (where Hosted Service is set to Yes). |
|
|
Enable |
Opens a confirmation box that lets you re-enable a Sentinel key that is disabled. > If the operation succeeds, you can download the V2CP file directly from the success message as well as from the grid. >If the operation fails, then follow the instructions in the error message. Available for: Sentinel HL (Driverless configuration) keys whose status is Disabled. |
| Clear 'Cloned' Status |
Opens a confirmation box that lets you clear the cloned status of a Sentinel key. >If the operation succeeds, the Sentinel key status to Enabled. You can download the V2CP file directly from the success message as well as from the grid. >If the operation fails, then follow the instructions in the error message. Available for: Sentinel keys whose status is Cloned. |
|
| Reset Virtual Clock |
Opens a confirmation box that lets you reset the virtual clock time on the Sentinel key to the current UTC time. >If the reset operation is successful, you can download the V2CP file directly from the success message as well as from the grid. >If the operation fails, then follow the instructions in the error message. Available for: Sentinel HL (Driverless configuration) and Sentinel SL keys whose status is Virtual Clock Error. |
|
|
|
Synchronize |
Connects to the service-hosted, cloud license manager server to synchronize a Sentinel key. Available for: CL keys that were generated using Produce and Push. |