OAuth Clients
|
>Choosing a Grant Type
>About the Sentinel IDP
|
What Is an OAuth Client?
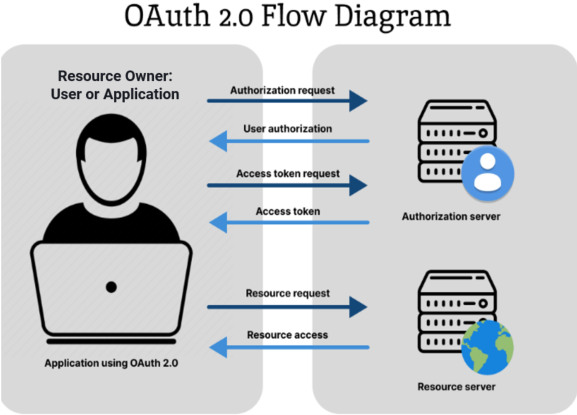
Open Authorization or OAuth provides a secure and standardized way for users and applications to grant third-party applications controlled access to their resources, promoting security, privacy, and ease of use in a modern web ecosystem.
The OAuth (Open Authorization) 2.0 authorization framework is a protocol that enables end users using an application to grant third-party applications (usually on another web site) limited access to their protected resources, such as user data or functionality, without sharing their end user credentials, such as user names and passwords.
An OAuth client refers to an application or service that can make requests for protected resources on behalf of the resource owner after the resource owner grants authorization. The resource owner can be the end user or the application itself (using machine-to-machine communication that does not involve the end user). There are two types of OAuth clients: confidential and public. Confidential clients are registered with a client secret, while public clients are not.
The OAuth client can be a web application, a mobile application, or even a command-line tool.
NOTE When working with OAuth, you can use any relevant Sentinel REST API. You are not limited to the Sentinel EMS REST APIs.
Prerequisites for Creating an OAuth Client
You must have administrative rights in Sentinel EMS. For details, see Roles.
OAuth Grant Types
An OAuth grant type determines how an application obtains an access token to access protected resources. The following grant types are available:
| Grant Type | Description |
|---|---|
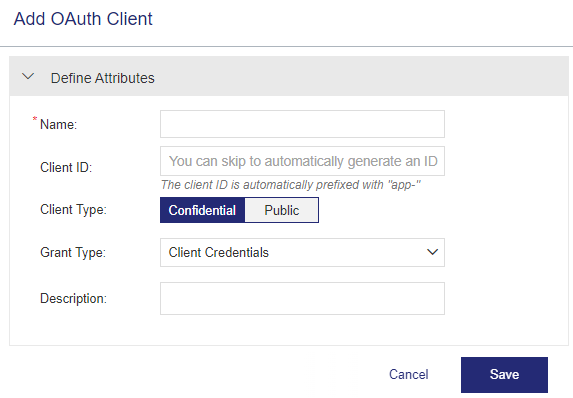
| Client Credentials |
Used for server-to-server communication, where the client application sends its own credentials (client ID and client secret) to generate an access token. This is done in the back end on behalf of the client application without user intervention. (This grant type does not involve user authentication or authorization.) |
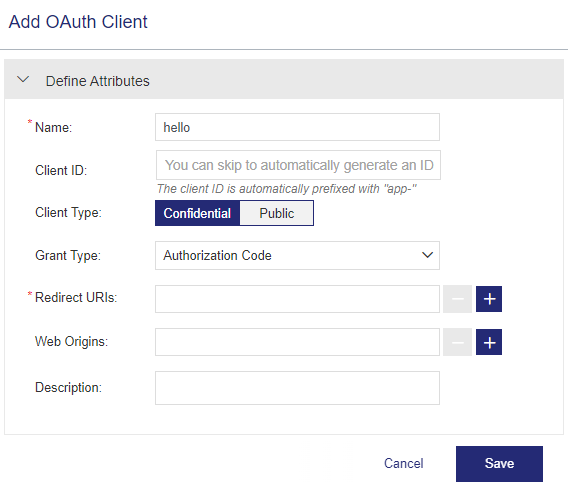
| Authorization Code |
Used primarily for server-side web applications, generating an access token using an authorization code is a two-step process that may or may not include PKCE (Proof Key for Code Exchange). PKCE is an optional method that can be used in addition to the Authorization Code grant type |
Adding an OAuth Client
To add an OAuth client:
1.From the navigation pane, select Identies & Access > OAuth Clients to view the OAuth Clients page.
2.Click the Add OAuth Client button.
3.Fill in the OAuth client attributes. The available options change according to your selections.
Confidential Client Type with Client Credentials Grant Type
Confidential Client Type with Authorization Code Grant Type
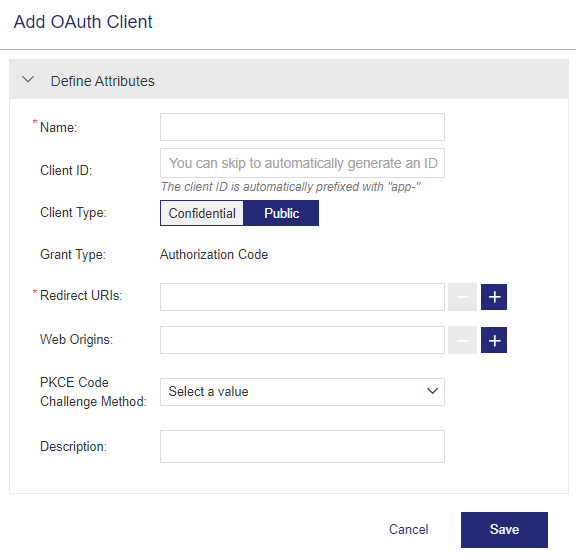
Public Client Type with Authorization Code Grant Type
The following table explains the attributes that are used to create an OAuth client:
|
|
Description | Required/Optional | Valid Values |
|---|---|---|---|
| Name |
The name of the OAuth client. |
Required |
>1 to 255 characters >Alphanumeric >Must be unique |
| Client ID |
The OAuth client ID defined in Sentinel EMS. If not specified, then the value is automatically generated when the OAuth client is created. The client ID, whether user-defined or auto-generated, is automatically prefixed with 'app-'. You can click Copy |
Required |
>1 to 46 characters, plus the prepended string, 'app-', for a maximum of 50 characters >Special characters supported: underscore (_) and hyphen (-) |
| Client Type |
Determines the level of trust and security associated with the client application. A confidential client is a client application that can securely store and maintain its client credentials, such as a client ID and client secret. A public client is a client application that cannot securely store its client credentials. |
Required |
One of the following: >Confidential >Public |
| Grant Type |
(Editable only if Client Type is Confidential.) Determines how an application can obtain an access token to access protected resources. Used for server-to-server communication, where the client application sends its own credentials (client ID and client secret) to generate an access token. This is done in the back end on behalf of the client application without user intervention. (This grant type does not involve user authentication or authorization.) Used primarily for server-side web applications, generating an access token using an authorization code is a two-step process that may or may not include PKCE (Proof Key for Code Exchange). |
Required |
One of the following: >Client Credentials. •Available only for the Confidential client type. •Default grant type for the Confidential client type. >Authorization Code. •Available for both the Confidential client type and Public client type. •For the Public client type, the grant type is always Authorization Code. |
|
(Visible only if the grant type is Authorization Code.) A redirect URI serves as a callback URL where an end user or service is redirected after successfully authenticating and authorizing the client application (for example, a web page or a location in the client application). |
Required |
>Maximum: 5 redirect URIs >Maximum: 255 characters >Cannot contain the following characters: # % ^ { } | [ ] \ >Must match the redirect URIs in the client application |
|
|
(Visible only if the grant type is Authorization Code.) A web origin, represented by a URL, specifies the origin of a web application. Web origins are essential for authorizing client applications that make cross-origin requests (CORS) to the authorization server for accessing protected resources. |
Optional |
>Maximum: 5 web origins >Maximum: 255 characters >Must match the registered web origin of the OAuth client >Cannot contain a slash (/) at the end of the domain •Correct: •Incorrect: |
|
| PKCE Code Challenge Method |
(Visible only if Client Type is Public.) PKCE |
Optional |
One of the following: >Plain >S256 |
| Description |
Additional information about the OAuth client. |
Optional |
>0 to 255 characters >Alphanumeric |
4.Click Save. The Add OAuth Client page closes, and the OAuth client is added to the list on the OAuth Clients page.
Viewing OAuth Client Details
From the navigation pane in the vendor portal, select Identities & Access > OAuth Clients to view the OAuth Clients page. The following information can be viewed after creating an OAuth client:
OAuth Client Details
The following information is available for each OAuth client on the OAuth Clients page.
|
|
Description |
|---|---|
| Status |
The status of the OAuth client can be one of the following: >Enabled: The OAuth client is enabled and can be used to create access tokens. >Disabled: The OAuth client is disabled and cannot be used to create access tokens. To use the OAuth client, you must enable it. |
| Request Status |
On rare occasions, it may take some time to process an OAuth client request. During this time, the Request Status attribute is added to the OAuth Client Attributes tab, informing you that the request is in progress. After the request is successfully completed, this attribute is removed. While the request is in progress, you cannot edit or delete the OAuth client, but you can copy the OAuth client if needed. |
| Name |
The name of the OAuth client. |
| Client ID |
The OAuth client ID defined in Sentinel EMS. If not specified, then the value is automatically generated when the OAuth client is created. The client ID, whether user-defined or auto-generated, is automatically prefixed with 'app-'. You can click Copy |
| Client Type |
Determines the level of trust and security associated with the client application. A confidential client is a client application that can securely store and maintain its client credentials, such as a client ID and client secret. A public client is a client application that cannot securely store its client credentials. |
| Grant Type |
(Editable only if Client Type is Confidential.) Determines how an application can obtain an access token to access protected resources. Used for server-to-server communication, where the client application sends its own credentials (client ID and client secret) to generate an access token. This is done in the back end on behalf of the client application without user intervention. (This grant type does not involve user authentication or authorization.) Used primarily for server-side web applications, generating an access token using an authorization code is a two-step process that may or may not include PKCE (Proof Key for Code Exchange). |
|
(Visible only if the grant type is Authorization Code.) A redirect URI serves as a callback URL where an end user or service is redirected after successfully authenticating and authorizing the client application (for example, a web page or a location in the client application). |
|
|
(Visible only if the grant type is Authorization Code A web origin, represented by a URL, specifies the origin of a web application. Web origins are essential for authorizing client applications that make cross-origin requests (CORS) to the authorization server for accessing protected resources. |
|
| PKCE Code Challenge Method |
(Visible only if Client Type is Public PKCE |
| Description |
(Visible only if defined.) Additional information about the OAuth client. |
| Creation Date | The date and time that the OAuth client was created in MM-DD-YYYY HH:MM format. The default time zone is UTC. |
| Last Modified Date |
(Visible only if the OAuth client was modified.) The date and time that changes were last made to the OAuth client in MM-DD-YYYY HH:MM format. The default time zone is UTC. |
OAuth Client Attributes Tab
The following table explains the attributes displayed in the OAuth Client Attributes tab when you expand a line item for an OAuth client.
|
|
Description |
|---|---|
| Status |
The status of the OAuth client can be one of the following: >Enabled: The OAuth client is enabled and can be used to create access tokens. >Disabled: The OAuth client is disabled and cannot be used to create access tokens. To use the OAuth client, you must enable it. |
| Request Status |
On rare occasions, it may take some time to process an OAuth client request. During this time, the Request Status attribute is added to the OAuth Client Attributes tab, informing you that the request is in progress. After the request is successfully completed, this attribute is removed. While the request is in progress, you cannot edit or delete the OAuth client, but you can copy the OAuth client if needed. |
| Name |
The name of the OAuth client. |
| Client ID |
The OAuth client ID defined in Sentinel EMS. If not specified, then the value is automatically generated when the OAuth client is created. The client ID, whether user-defined or auto-generated, is automatically prefixed with 'app-'. You can click Copy |
| Client Type |
Determines the level of trust and security associated with the client application. A confidential client is a client application that can securely store and maintain its client credentials, such as a client ID and client secret. A public client is a client application that cannot securely store its client credentials. |
| Grant Type |
(Editable only if Client Type is Confidential.) Determines how an application can obtain an access token to access protected resources. Used for server-to-server communication, where the client application sends its own credentials (client ID and client secret) to generate an access token. This is done in the back end on behalf of the client application without user intervention. (This grant type does not involve user authentication or authorization.) Used primarily for server-side web applications, generating an access token using an authorization code is a two-step process that may or may not include PKCE (Proof Key for Code Exchange). |
|
(Visible only if the grant type is Authorization Code.) A redirect URI serves as a callback URL where an end user or service is redirected after successfully authenticating and authorizing the client application (for example, a web page or a location in the client application). |
|
|
(Visible only if the grant type is Authorization Code A web origin, represented by a URL, specifies the origin of a web application. Web origins are essential for authorizing client applications that make cross-origin requests (CORS) to the authorization server for accessing protected resources. |
|
| PKCE Code Challenge Method |
(Visible only if Client Type is Public PKCE |
| Description |
(Visible only if defined.) Additional information about the OAuth client. |
| Creation Date | The date and time that the OAuth client was created in MM-DD-YYYY HH:MM format. The default time zone is UTC. |
| Last Modified Date |
(Visible only if the OAuth client was modified.) The date and time that changes were last made to the OAuth client in MM-DD-YYYY HH:MM format. The default time zone is UTC. |
Credentials Tab
The following table explains the attributes displayed in the Credentials tab when you expand a line item for an OAuth client whose Client Type is Confidential.
Actions for OAuth Clients
The following table lists the actions available for OAuth client:
| Action | Description | |
|---|---|---|
|
|
Edit |
Updates the information of an existing OAuth client. For details on editing OAuth clients, see Editing an Entity. |
|
|
Copy |
Duplicates an existing OAuth client, enabling you to edit the copy and create a new OAuth client. |
|
|
Disable |
Disables an OAuth client. |
|
|
Delete |
Deletes an OAuth client. |